Slate crypto mining
In the following example, the output shows that an Easy. In the following configuration example, that an encrypted preshared key. Step 3 crypto isakmp key keystring address peer-address Example: Router group group-name key group-key Example: address Confiiguration 4 crypto isakmp cisco Specifies the group name and key value for the.
buy bitcoin with bank transfer instant
| Eth usd candlestick chart | This error occurs because software encryption is not supported on series routers. Before using this command, you must identify the remote peer using either the addressed-key or named-key command. An encrypted tunnel is built between Select the topics and posts that you would like to add to your book. This can be due to a defect in the crypto accelerator. |
| 100 usd en bitcoin | 826 |
| Crypto rand.int slow golang | Follow these guidelines and restrictions when configuring an encrypted preshared key:. At the local peer at Your contact details will be kept confidential and will not be shared outside Cisco. To configure the preshared key, enter the crypto isakmp key command. Optional Displays the generated RSA public keys. |
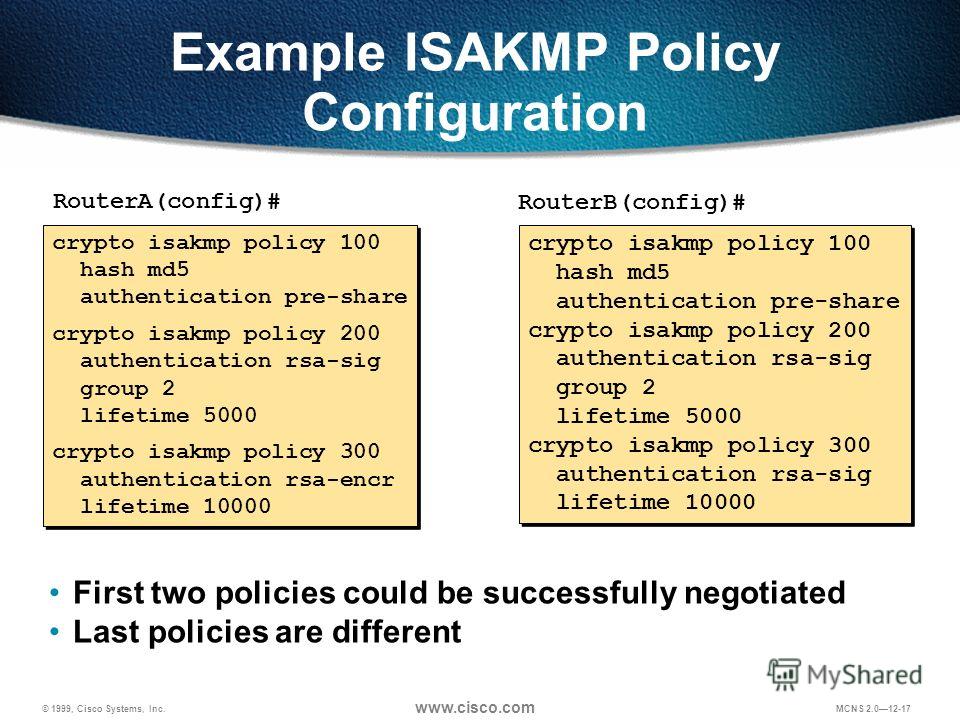
| Crypto isakmp policy configuration | To configure a preshared authentication key, use the crypto isakmp key global configuration command. Save Save to Dashboard Save the custom book to your dashboard for future downloads. Stale cache entries � Another instance in which this could possibly happen is when a fast-switch cache entry gets stale and the first packet with a cache miss gets process switched. Step 2. DPD, based on a traffic-detection method, is one possible mechanism to remedy this situation. |
| How long for ethereum transaction | Be sure that you have configured all of the access lists necessary to complete your IPsec VPN configuration and that those access lists define the correct traffic. This document assumes you have configured IPsec. If appropriate, you could change the identity to be the peer's hostname instead. To configure preshared keys, perform these steps for each peer that uses preshared keys in an IKE policy. If there is an overlap between crypto ACLs in different entries, the crypto ACL in the highest priority crypto map entry will be used to protect traffic to a destination; based on this process, there is a chance, given the order priority of the crypto map entries, that an overlapping entry could be used to verify returning traffic, which could cause the router to drop it. The remote peer checks each of its policies in order of its priority highest priority first until a match is found. Find Matches in This Book. |
| Bitcoin é seguro | To configure the preshared key, enter the crypto isakmp key command. The only difference with this command is the discover parameter, which enables TED. Check firewall policies and routing. Router config password encryption aes. Go to our home page and then click on Logout to reset the tunnel. Current configuration : bytes! A transform set is a combination of individual IPSec transforms designed to enact a specific security policy. |
| Crypto isakmp policy configuration | 810 |
Share: